Hello readers! Today I will be writing a general post which I think can be helpful for the SOC analysts while creating incidents. So, let’s first understand what this article is about and how it will help you in your process. So, ATP safe links is actually a security feature of Microsoft that comes with Office 365 for the enterprise organizations. According to Microsoft, ATP safe links can help the organization in identifying the malicious URL.
What are ATP Safe Links?
Microsoft’s ATP Safe Links work by rewriting the actual URLs in an incoming email with URLs like (*.outlook.com). And by this it allows the Microsoft to first scan the original incoming link in their sandbox to look for anything suspicious and then redirects it to the user if the link turns out to be safe to browse. For example, an email containing a link to tech-zealots.com will be replaced with:-
“na01.safelinks.protection.outlook.com/?url=http%3a%2f%2ftech-zealots.com”
So whenever you click on this link, Microsoft ATP will first scan the link for any maliciousness before redirecting it to the end user’s browser. It checks if that link:-
- Is not on a custom blacklist created by the organization.
- Is not on Microsoft’s blacklist.
Also, if the URL leads to an attachment it will be scanned by the Microsoft for the presence of Malware. And after that, the user is taken to a page displaying a warning message asking them if they wish to continue to the unsafe domain.
How to Identify Actual URL?
- It is obvious that it becomes very much difficult to identify the actual URL when the given URL is too long and gibberish as well. Sometimes it happens that a full URL also contains the redirected actual URL. But to identify that the actual redirected URL is a tricky task. So what you can do is that you can grab full URL and run it in https://urlscan.io and look for the effective URL section.
- Also sometimes you will receive a URL that is fully encoded. For e.g. this URL “https%3A%2F%2Ftech-zealots.com%2Fthreat-lab%2Foffice-365s-atp-security-feature-creating-havoc%2F” is pretty much long and encoded. So what you can do is you can directly grab that full URL and can decode it with the help of several decoders online. I would recommend you to use URL Encoder/Decoder for that.
Problem Area
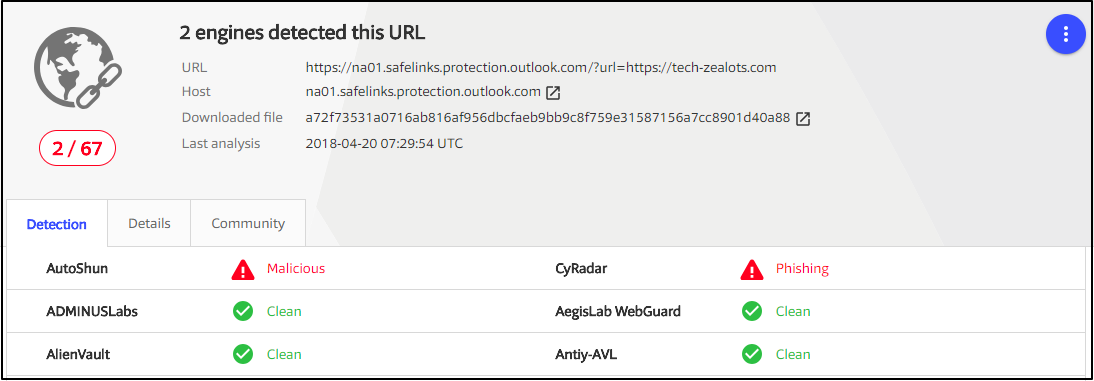
This is what we are seeing in our daily Spam box and many of you will be creating INCs on the basis of domain “na01.safelinks.protection.outlook.com” but in actual the Incident should be created on the basis of effective URL.
For example, if you happen to receive a URL “hxxps://na01.safelinks.protection.outlook.com/?url=http%3A%2F%2Ftech-zealots.com” in which a part of the URL “hxxps://na01.safelinks.protection.outlook.com” is actually a security feature of Microsoft ATP and you should perform your investigation on the remaining part of the link i.e. “http%3A%2F%2Ftech-zealots.com”.
Also if you scan the above link “hxxps://na01.safelinks.protection.outlook.com/?url=http%3A%2F%2Ftech-zealots.com” in VirusTotal then you will receive the result that shows that 2 AVs have flagged the URL. But in actual it’s a False Positive.
NOTE:- I deliberately used “tech-zealots.com” above just to give you an idea that one should not trust the result of any security tool 100%. Most of the tools operate on the basis of inbuilt security signature and these signatures can be bypassed as well.