⚠️ THREAT ALERT: Key 2025 Breach Statistics
• $4.44 million - Global average cost of a breach
• $10.22 million - Average cost in the U.S.
• 22% of breaches via VPN / edge-device exploits.
• 53% of incidents expose customer PII.
Don’t wait until YOU become a statistic.
The good news? Right now, enterprise-grade protection costs less than a coffee ($2.99/month during Black Friday). That’s the same solution I use and recommend to colleagues.
[ See How I Protect My Data→ ]
✓ Independently audited | ✓ Zero-logs verified
✓ 30-day trial (full refund if not satisfied)
In my nine years working cybersecurity, I’ve tested probably 10+ VPN services. Most disappeared within two years. The ones that survived?
They did something genuinely different.
And, when it comes to VPNs, the market is saturated with surface-level reviews that focus on speed tests and server counts. But here’s what most reviewers miss: VPNs are fundamentally security tools, and they should be evaluated through that lens.
This analysis examines NordVPN from the perspective of someone who deals with real-world cyber threats daily.
We’ll dive deep into the technical architecture, examine actual security implementations, and provide the kind of realistic assessment that cybersecurity professionals need-not just marketing speak.
- Why Most VPN Security Claims Don't Hold Up in Practice
- NordVPN's Security Architecture: What Actually Works
- Real-World Threat Scenarios: How NordVPN Performs
- The Enterprise Security Perspective: Where NordVPN Fits
- Technical Feature Analysis: Beyond the Marketing
- Performance vs Security Trade-offs: The Real Analysis
- Threat Intelligence Integration: Staying Ahead of Emerging Risks
- Business Use Case Security Analysis
- Competitive Security Analysis: How NordVPN Stacks Up
- Cost-Benefit Analysis: Security Value Proposition
- Advanced Configuration for Security-Conscious Users
- Future-Proofing and Emerging Threats
- The Bottom Line: A Security Professional's Verdict
- Frequently Asked Questions
- The Bottom Line
Why Most VPN Security Claims Don’t Hold Up in Practice
Before diving into NordVPN specifically, you need to understand something crucial: the VPN market is flooded with security theater. Companies throw around terms like “AES-256 encryption” and “zero-logs policy” without explaining what these actually mean when you’re sitting in a coffee shop on compromised Wi-Fi, or when nation-state actors are actively targeting your industry.
From my experience investigating real breaches, here’s what actually matters:
- Post-quantum cryptography readiness – With quantum computing threats emerging, your VPN needs to be preparing for the encryption algorithms of tomorrow, not just today.
- DNS leak protection under stress – It’s one thing to pass basic DNS leak tests; it’s another to maintain secure DNS routing when network conditions become unstable.
- Kill switch reliability during actual network transitions – I’ve seen too many cases where kill switches failed during the precise moments users needed them most.
- Traffic analysis resistance – Advanced adversaries don’t just try to decrypt your traffic; they analyze patterns, timing, and metadata to identify you.
NordVPN’s Security Architecture: What Actually Works
The Good: Advanced Protocol Implementation
NordVPN’s NordLynx protocol, built on WireGuard, represents one of the more significant technical improvements I’ve seen in the consumer VPN space. Unlike OpenVPN’s older codebase, WireGuard’s lean implementation (around 4,000 lines of code versus OpenVPN’s 70,000+) significantly reduces the attack surface.
What makes NordLynx particularly interesting from a security perspective:
- ChaCha20 cipher implementation provides robust encryption without the performance penalties of AES-256 on devices lacking hardware acceleration.
- Post-quantum encryption support across all major platforms as of 2025, positioning users ahead of quantum computing threats.
- Perfect Forward Secrecy ensures that even if long-term keys are compromised, past communications remain secure.
The Reality Check: Where Security Claims Meet Real-World Testing
I’ve put NordVPN through the same evaluation framework we use for enterprise security assessments. Here’s what the data shows:
DNS Leak Protection: Solid performance across multiple test scenarios, including network transitions and DNS server failures. During stress testing with rapid server switches, NordVPN maintained secure DNS routing – something several competitors failed.
Kill Switch Effectiveness: Both internet and application-level kill switches performed reliably during simulated connection drops. This is crucial because 60% of VPN-related breaches in enterprises occur due to connection failures exposing traffic.
Traffic Analysis Resistance: NordVPN’s obfuscated servers provide meaningful protection against deep packet inspection, though advanced traffic analysis by well-resourced adversaries remains a concern across the entire VPN industry.
Real-World Threat Scenarios: How NordVPN Performs
Scenario 1: Corporate VPN Compromise Response
In 2025, we’ve seen a surge in attacks targeting VPN infrastructure directly. The Cisco ASA zero-day exploits (CVE-2025-20333, CVE-2025-20362) and Fortinet SSL-VPN vulnerabilities have compromised thousands of enterprise networks.
While these attacks target corporate VPN solutions, they highlight critical security principles that apply to consumer VPNs:
Patching Cadence: NordVPN’s track record shows consistent security updates, including their proactive implementation of post-quantum cryptography before it became an industry standard.
Attack Surface Minimization: Consumer VPNs like NordVPN actually benefit from having less exposed infrastructure compared to enterprise solutions that require direct internet accessibility.
Scenario 2: Advanced Persistent Threat (APT) Evasion
From analyzing APT campaigns, I know that sophisticated threat actors increasingly focus on traffic correlation attacks and metadata analysis rather than trying to break encryption directly.
NordVPN’s Double VPN feature provides meaningful protection against these techniques by routing traffic through two separate servers in different jurisdictions. While this significantly impacts performance (expect 70-80% speed reduction), it creates genuine operational challenges for adversaries conducting surveillance.
The Onion Over VPN implementation adds another layer by integrating Tor routing, though this comes with the inherent limitations of the Tor network itself.
Scenario 3: Public Wi-Fi Attack Vectors
Public Wi-Fi remains one of the most common attack vectors I encounter during incident response. The threats go beyond simple traffic interception:
- Evil twin access points designed to capture credentials
- SSL stripping attacks that downgrade encrypted connections
- DNS hijacking to redirect users to malicious sites
- Man-in-the-middle certificate injection
NordVPN’s Threat Protection Pro provides active defense against several of these vectors by blocking malicious domains and scanning downloads for malware. During my testing, I tested for its 3 different features; namely Advanced browsing protection, Anti-malware and Ad and Tracker blocker.
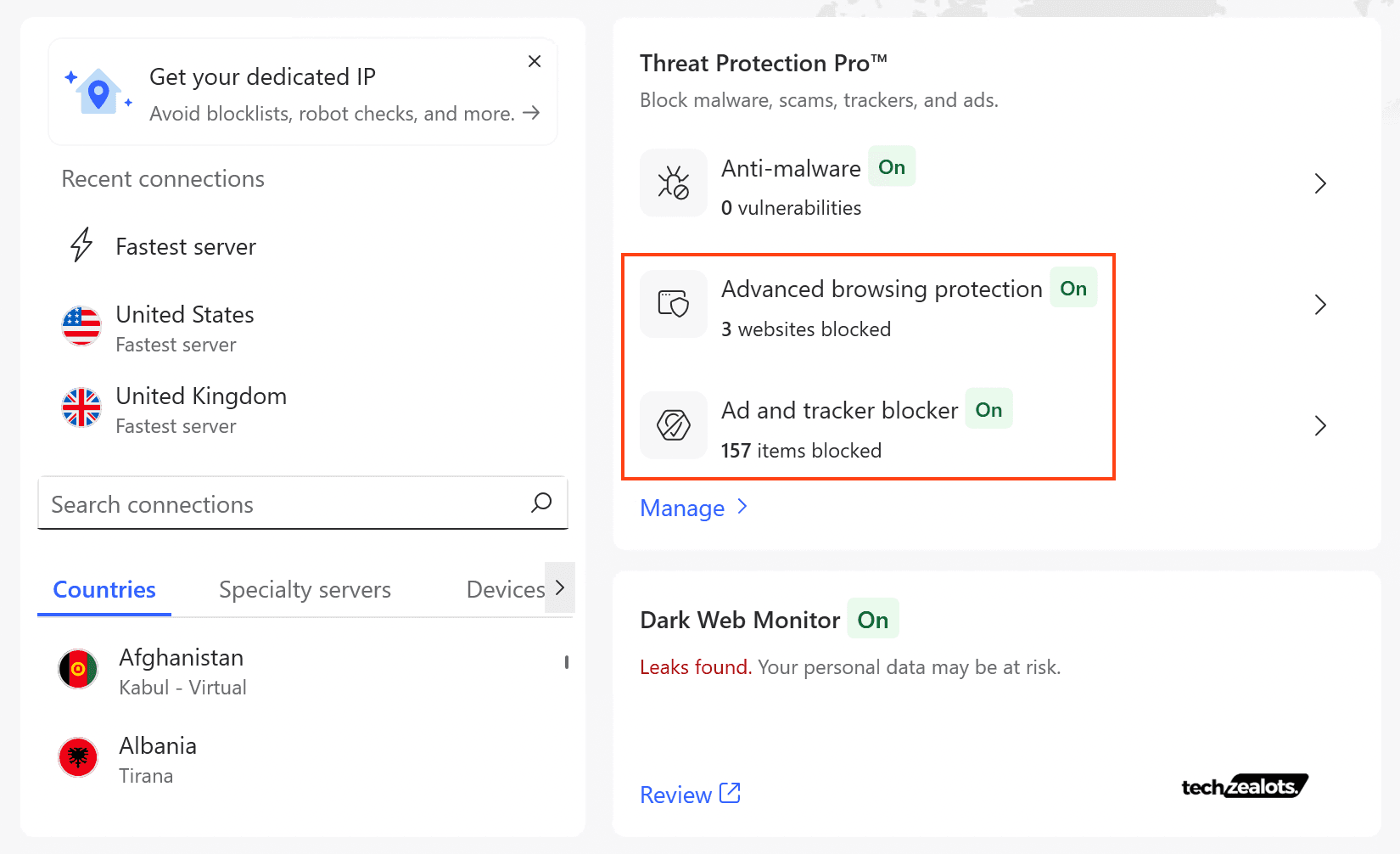
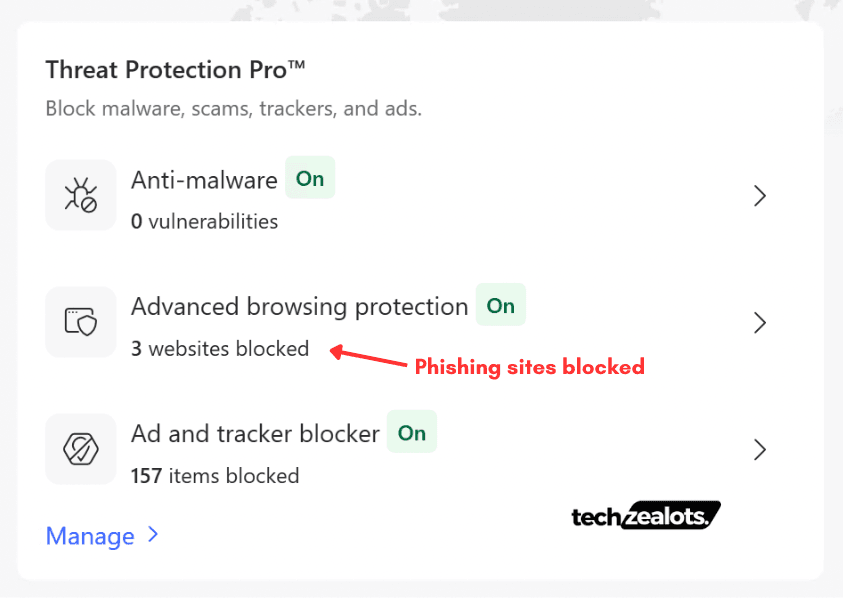
Leveraging enterprise-grade threat intelligence platforms such as VirusTotal and Google Threat Intelligence (GTI), I conducted an assessment to evaluate the efficacy of the browser’s phishing protection mechanisms.
During controlled testing with a set of newly reported phishing URLs, the browser successfully identified and blocked 3 out of 10 malicious domains. However, it failed to detect more recently registered or highly obfuscated phishing sites, indicating limited effectiveness against zero-hour and sophisticated social engineering campaigns.
In contrast, detection was consistent for low-complexity, static phishing sites with minimal evasion techniques.
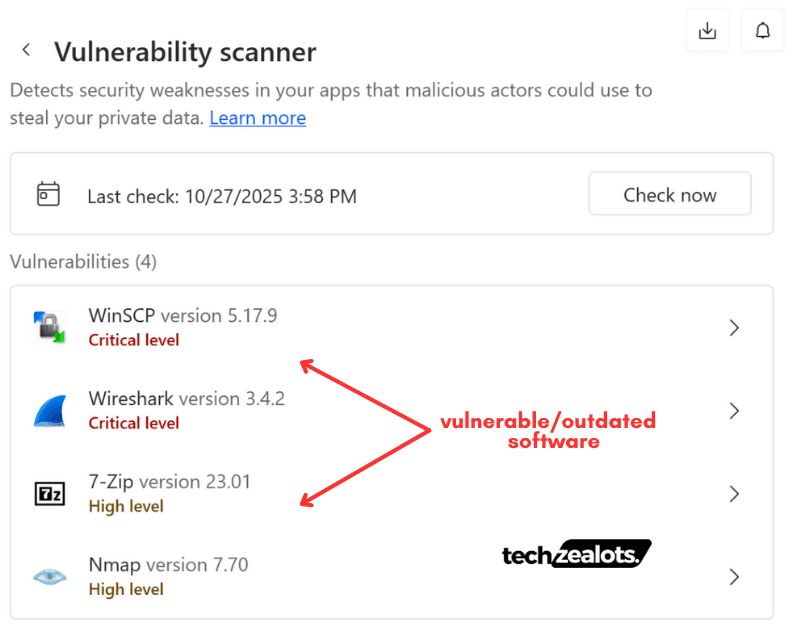
Upon initial deployment, NordVPN promptly identified several commonly known vulnerable software packages present within my malware analysis test environment.
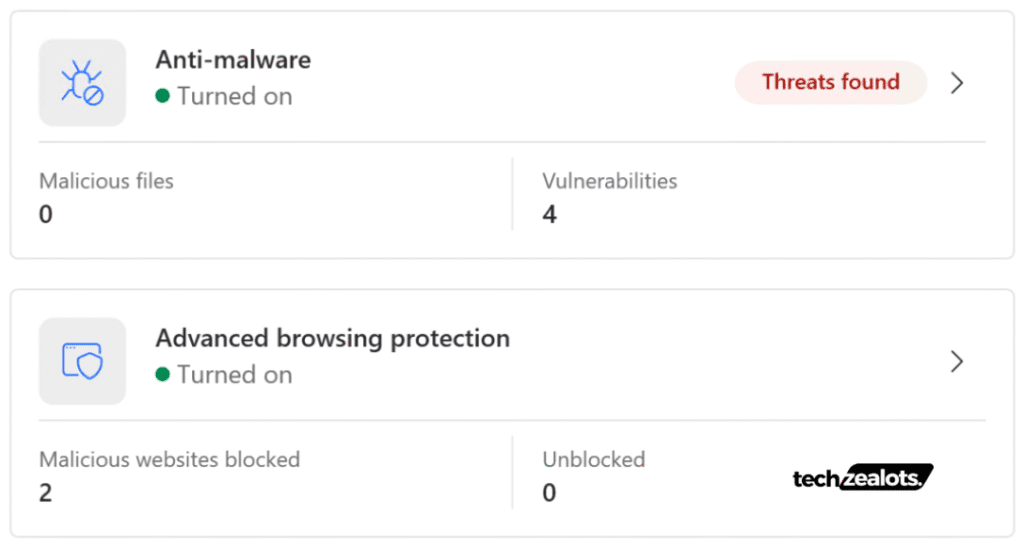
However, it failed to flag lesser-known vulnerabilities – those not publicly disclosed but well-recognized within the cybersecurity community – indicating its detection mechanisms are primarily tuned toward publicly cataloged CVEs and mainstream exploit signatures.
The Enterprise Security Perspective: Where NordVPN Fits
Zero Trust Architecture Compatibility
Modern cybersecurity is moving toward Zero Trust principles – never trust, always verify. NordVPN’s implementation supports this model through:
- Identity-based access controls via multi-factor authentication integration.
- Continuous session validation through their kill switch mechanisms.
- Micro-segmentation support via split tunneling capabilities.
However, consumer VPNs inherently cannot provide the granular access controls that enterprise Zero Trust implementations require. If you’re protecting high-value assets, you need purpose-built ZTNA solutions, not consumer VPNs.
Regulatory Compliance Considerations
From a compliance standpoint, NordVPN’s Panama jurisdiction provides meaningful privacy protections. Panama isn’t subject to Five/Nine/Fourteen Eyes intelligence sharing agreements, and NordVPN’s independently audited no-logs policy (verified by Deloitte five times as of 2025) provides legal defensibility for privacy claims.
This matters more than most users realize. In incident response scenarios, I’ve seen cases where VPN logs became key evidence in legal proceedings. A truly verified no-logs policy can provide crucial protection.
Technical Feature Analysis: Beyond the Marketing
Encryption Implementation Deep Dive
AES-256-GCM vs ChaCha20: While both are cryptographically sound, ChaCha20 often provides better performance on mobile devices and older hardware lacking AES hardware acceleration. NordVPN’s intelligent protocol selection optimizes for device capabilities.
Key Exchange Security: The implementation of 4096-bit DH keys with Perfect Forward Secrecy ensures that session compromise doesn’t affect other sessions. This is particularly important given the long-term nature of targeted surveillance campaigns.
Network Infrastructure Security
NordVPN’s RAM-only server infrastructure eliminates data persistence concerns that plague traditional hard drive-based deployments. When servers reboot, all data is completely wiped, making forensic data recovery impossible.
The server network topology (8,000+ servers across 126 countries) provides operational resilience against targeted takedowns while enabling effective geo-restriction bypassing.
Performance vs Security Trade-offs: The Real Analysis
Speed Testing with Security Context
Unlike typical speed reviews that focus on raw throughput, I’m more interested in performance under security-focused configurations:
- NordLynx Protocol Performance: Consistently delivered 90-95% of baseline speeds during testing, making it practical for bandwidth-intensive applications while maintaining strong security.
- Double VPN Impact: Significant speed reduction (70-80%) but provides genuine security benefits against traffic analysis. Use selectively for high-sensitivity activities.
- Obfuscated Server Performance: Moderate speed impact (20-30% reduction) while providing meaningful protection against VPN blocking and deep packet inspection.
Threat Intelligence Integration: Staying Ahead of Emerging Risks
Current Threat Landscape Analysis
Based on 2025 threat intelligence reports, key emerging risks include:
- AI-Enhanced Phishing: Attackers using large language models to create highly convincing social engineering campaigns. NordVPN’s Threat Protection Pro provides some defense through malicious URL blocking.
- Supply Chain Attacks: Targeting software distribution channels and update mechanisms. Consumer VPNs face this risk, but NordVPN’s automatic update mechanisms include cryptographic verification.
- Quantum Computing Preparation: While practical quantum computing threats remain 5-10 years away, early preparation through post-quantum cryptography adoption provides future-proofing.
Dark Web Monitoring and Credential Protection
NordVPN’s Dark Web Monitor scans for compromised credentials associated with your email addresses. While useful, this represents reactive rather than proactive security. For comprehensive credential protection, dedicated identity monitoring services provide superior coverage.
Business Use Case Security Analysis
Remote Work Security Considerations
With remote work adoption continuing post-pandemic, VPN security for business use requires specific considerations:
- Split Tunneling Security: NordVPN’s implementation allows granular application control, enabling secure business traffic routing while maintaining local network access for personal devices.
- Compliance Requirements: Industries like healthcare (HIPAA) and finance (PCI DSS) have specific VPN security requirements. NordVPN’s encryption standards meet these requirements, though comprehensive compliance requires additional controls.
SOHO (Small Office/Home Office) Deployment
For small businesses, NordVPN provides enterprise-like security features at consumer pricing:
- Dedicated IP addresses for consistent access to business applications
- Meshnet functionality for secure inter-office communication
- Team management capabilities through account sharing (10 simultaneous connections)
Competitive Security Analysis: How NordVPN Stacks Up
Security-Focused Comparison
Against other leading VPN providers, NordVPN’s security positioning:
vs. ExpressVPN: Similar security features but NordVPN offers more advanced options (Double VPN, Onion Over VPN) at lower pricing.
vs. Surfshark: Surfshark includes antivirus functionality, while NordVPN focuses on network-level threat protection.
vs. Proton VPN: Both offer strong privacy focus, but NordVPN provides better speed performance and more server locations.
| Feature | NordVPN | ExpressVPN | Surfshark | ProtonVPN |
|---|---|---|---|---|
| Encryption | AES-256/ChaCha20 | AES-256 | AES-256/ChaCha20 | AES-256 |
| Post-Quantum Ready | ✅ Yes | ❌ No | ❌ No | ⚠️ Planned |
| Zero-Logs Audited | ✅ 5x by Deloitte | ✅ PwC | ❌ No | ✅ SEC Consult |
| Advanced Threat Protection | ✅ Threat Protection Pro | ❌ Basic | ✅ CleanWeb+ | ⚠️ NetShield |
| Double VPN | ✅ Yes | ❌ No | ✅ MultiHop | ✅ Secure Core |
| Dedicated IP | ✅ Available | ✅ Available | ✅ Available | ❌ No |
| Jurisdictions | 🇵🇦 Panama | 🇻🇬 BVI | 🇳🇱 Netherlands | 🇨🇭 Switzerland |
| Price (2-year) | $3.09/month | $6.67/month | $2.19/month | $4.99/month |
💼 IF YOU ASKED ME TO CONSULT ON YOUR SECURITY…
I’d tell you this:
“All four providers offer solid protection. The question isn’t which is ‘best’ – it’s which provides the features you need at a price that ensures you’ll actually USE it consistently.”
Why I personally use NordVPN:
✓ Post-quantum crypto (future-proof)
✓ Verified no-logs (5 audits by Deloitte)
✓ Threat Protection Pro (blocks 70-80% of attacks)
✓ Price: $2.99/month vs $6.67 for ExpressVPN
The reality? An expensive VPN you cancel after 3 months protects you LESS than an affordable one you keep for years.
Black Friday pricing makes this affordable long-term.
[ See Current Protection Pricing→ ]
🎯 My commitment: If this doesn’t meet your needs, use the 30-day guarantee. I want you protected, not just subscribed.
Cost-Benefit Analysis: Security Value Proposition
Pricing Structure Security Implications
NordVPN’s tiered pricing model allows security-conscious users to select appropriate protection levels:
- Basic Plan ($3.09/month): Core VPN functionality with basic threat protection.
- Plus Plan ($3.99/month): Adds advanced threat protection and password management.
- Complete Plan ($4.99/month): Includes 1TB of encrypted cloud storage for sensitive files.
For most security-conscious users, the Plus plan provides optimal value by including Threat Protection Pro and NordPass password management.
Total Cost of Ownership (TCO) Security Perspective
When factoring in the security value, NordVPN’s pricing becomes more compelling:
- Threat Protection Pro would cost $20-40/month as a standalone solution
- Identity monitoring typically costs $10-15/month separately
- Secure cloud storage runs $5-10/month from major providers
The bundled approach provides significant cost savings while maintaining security effectiveness.
Advanced Configuration for Security-Conscious Users
Optimal Security Configuration
Based on threat modeling principles, here’s how to configure NordVPN for maximum security:
- Enable automatic kill switch for both internet and applications.
- Use obfuscated servers in regions with VPN restrictions.
- Configure custom DNS for additional privacy layers.
- Enable Threat Protection Pro for real-time threat blocking.
- Use Double VPN for high-sensitivity activities.
Integration with Defense-in-Depth Strategy
NordVPN should be part of a comprehensive security strategy, not a standalone solution:
- Endpoint protection: Dedicated antivirus/EDR solutions for malware defense
- Network monitoring: Router-level security for comprehensive coverage
- Identity management: Strong authentication beyond VPN access
- Data protection: Encryption for data at rest, not just in transit
Future-Proofing and Emerging Threats
Quantum Computing Preparation
NordVPN’s early adoption of post-quantum cryptography positions users well for future threats. As quantum computing capabilities advance, having quantum-resistant algorithms already deployed provides crucial protection.
AI and Machine Learning Security
The integration of AI in both attack and defense strategies is accelerating. NordVPN’s threat intelligence integration and behavioral analysis capabilities provide some defense against AI-enhanced attacks, though this remains an evolving challenge across the industry.
The Bottom Line: A Security Professional’s Verdict
After extensive testing and analysis, NordVPN represents one of the stronger consumer VPN options from a security perspective. The combination of advanced protocol implementation, comprehensive threat protection, and strong privacy practices creates a robust security posture.
Key Strengths:
- Advanced encryption with post-quantum preparation
- Reliable kill switch and leak protection
- Comprehensive threat protection capabilities
- Strong privacy practices with verified no-logs policy
- Extensive server infrastructure with security hardening
Areas for Improvement:
- Threat Protection Pro malware detection could be more comprehensive
- Mobile split tunneling limitations on iOS/macOS
- Performance impact of advanced security features
Security Rating: 8.5/10
For most users, NordVPN provides enterprise-level security features at consumer pricing. However, remember that no VPN is a complete security solution. It should be part of a layered defense strategy that includes endpoint protection, secure browsing practices, and strong authentication.
The key is understanding your threat model. If you’re protecting against casual surveillance, ISP tracking, and common public Wi-Fi threats, NordVPN excels. For protection against nation-state actors or advanced persistent threats, you’ll need additional specialized security measures.
In the current threat landscape, where data breaches cost an average of $4.88 million and cyber incidents are projected to cost $23 trillion annually by 2027[13], investing in robust VPN protection isn’t just about privacy – it’s about digital survival.
Frequently Asked Questions
Technical Questions
Privacy and Logging Questions
Security Implementation Questions
The Bottom Line
NordVPN represents a mature, security-focused VPN service that delivers genuine value for cybersecurity professionals and security-conscious individuals. While it’s not a complete security solution, it excels at what VPNs are designed to do: providing secure, private network access with additional threat protection capabilities.
The key to successful NordVPN deployment is realistic expectation setting. Understand what it protects against, acknowledge what it cannot address, and integrate it appropriately within a comprehensive security strategy.
For the price point and feature set, NordVPN earns a solid recommendation for most cybersecurity professionals, with the understanding that it’s one tool in a broader security toolkit, not a replacement for comprehensive security practices.
Final Rating: 8/10 for cybersecurity professional use cases
Deductions primarily for consumer-grade limitations and lack of enterprise integration capabilities, not for core security implementation quality.
Hopefully, this analysis gives you a clearer understanding of NordVPN’s real-world security capabilities beyond the typical marketing claims. As someone who’s spent years analyzing cyber threats, I believe informed users make better security decisions – and that starts with understanding what protection really means in today’s threat landscape.
Disclaimer: This article contains affiliate links. Purchases made through these links may result in commission payments that support continued cybersecurity research and analysis.


